
 Chip Services
Chip Services

 Products
Products
- Automotive and Industrial control
- Information Security
- Edge Computing& Network Communication
Products

 Resources
Resources

 Language
Language
The cloud security chip of CCP907T series are high-performance single-core microprocessors. It is designed based on the C9000 PowerPC core with 4-issue, 9-stage pipeline and superscalar architecture, supporting SMP systems. In addition, various peripherals are integrated on-chip, such as PCI-E、USB、GPIO、SPI、UART, etc.
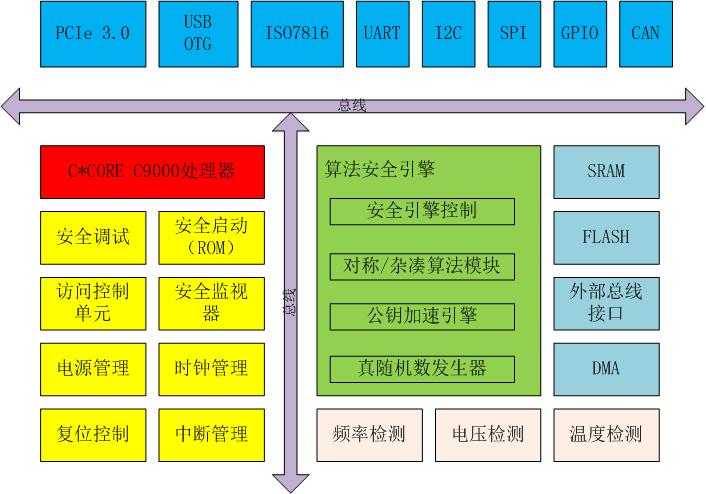
Cloud Security Chip-CCP907T Series
Package Type
| Interface | Package type and pin assignment(mm) |
CCP907T-FF BGA485(17*17) | |
SPI | 3 |
SSI | 1 |
I2C | 3 |
UART | 2 |
ISO7816 | 1 |
EBC | 1 |
TRNG | 1 |
JTAG | 1 |
CAN | 3 |
USB-OTG | 3.0 |
USB2.0-OTG | 1 |
PCI-E 2.0 | x4 support EP & RC mode |
GPIO | support |
• 4-issue RISC architecture
• 9-stage pipeline
• Super scalar
• 32KB data CACHE
• 32KB instruction CACHE
• 256KB L2 CACHE
• 512KB byte SRAM
• 1MB byte FLASH
• Voltage detection unit
• Frequency detection unit
• Temperature detection unit
• Power supply burr detection unit
• Light detection unit
• Physical detection protection
• Unique serial number for each product
• Power domain: 0.8V 1.8V, 3.3V
• Commercial grade operating temperature:0-70 degrees
• Industrial grade operating temperature:-40~85 degrees
• Boot Rom: Secure boot, authenticated encryption protection for user code
• Security debugging control: configurable debugging interface for open and close
• Access control unit: authorized access control to address space
• Security Monitor: all security information be monitored and collected in real time
• A random root key in side to encrypt and protect the application system key
• Symmetric algorithms: SM4/AES/DES/3DES
• Asymmetric algorithms: SM2/ SM9/RSA1024/RSA204
• Hashing algorithms: SM3/SHA1/SHA256/SHA384/SHA512/HMAC
• Hardware algorithm engine independent of CPU
• Protection from non-authorized access of data stored in non-volatile memory and for data integrity
• True random number generator, internal multi-channel physical random source, CPU and algorithm engine can be independently running.
• Level I of security chip for commercial crypto product certification

• PCI-E crypto card
• Signature/verification server
• Secure Gateway
• Firewall
• Trusted computing
• 5G communication security
• Surveillance

• Complete development environment
• Rich driver libraries
• Complete application solutions